In this tutorial i will explain how to automatically enroll your Windows 10/11 domain joined PC’s into Intune using a Group Policy Object.
Note: if you are using Azure MFA make sure you read the ‘known issues’ section at the end of the article or you will run into issues
Before we begin, there’s a few prerequisites that you must meet in order for devices to be automatically joined to Intune.
- Devices must be Hybrid Azure AD joined (HAADJ)
- User(s) must be permitted to enroll devices into Azure AD have a valid Intune Licence
Setup Hybrid Azure AD Join
If your devices are not already configured to Hybrid Join you will need to install the Azure AD Connect Tool on to a server on your domain.
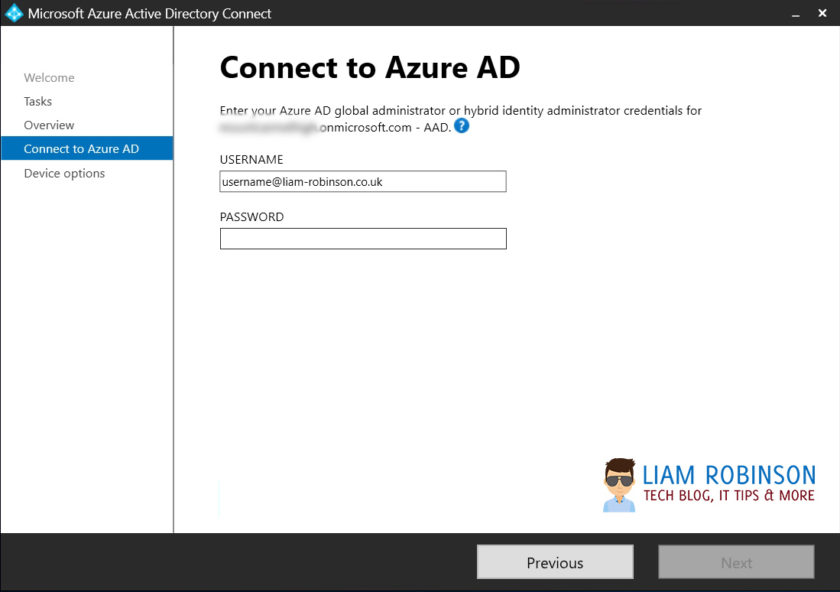
- Launch Azure AD Connect tool and click configure.
- Click Configure Device Options
- Authenticate with your Azure Admin account, if using AAD Connect Version 1.6.2.4 or above, you can use an account with the ‘Hybrid Identity Admin‘ role assigned instead.
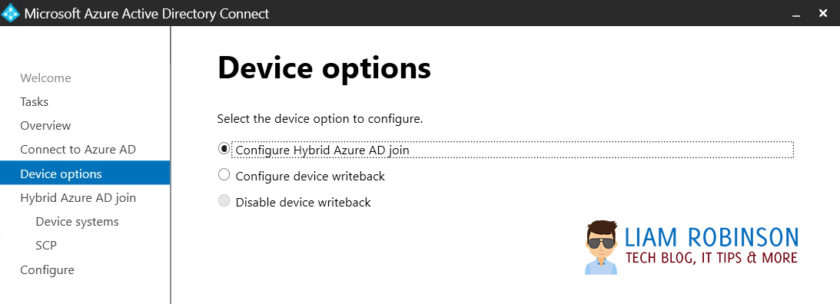
4. Select Configure Hybrid Azure AD Join from the options
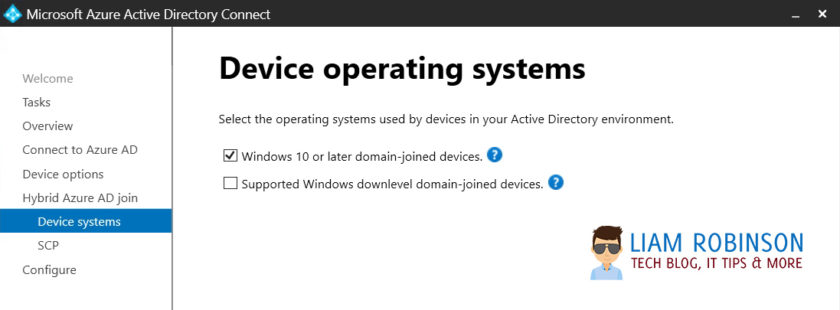
5. Tick ‘Windows 10 or later domain joined devices‘ and click ‘Next‘ – You don’t need to choose windows down level devices as this wont work with automatic enrollment anyway.
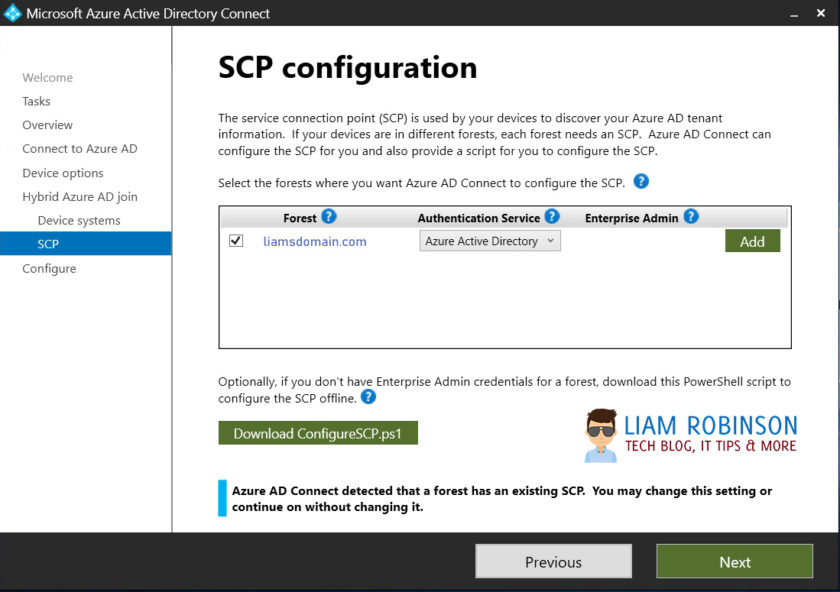
5. In order for your devices to know which Azure Tennant to join you must first specify a SCP or Service Connection Point. Azure AD Connect tool will populate this for you but first you need to provide enterprise admin credentials for your Active Directory forest. Tick your forest and press add, providing enterprise admin credentials.
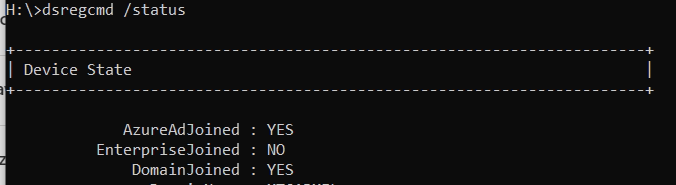
You can verify your device is Azure AD Joined by running dsregcmd /status in a command prompt
| AzureAdJoined | EnterpriseJoined | DomainJoined | Device state |
|---|---|---|---|
| YES | NO | NO | Azure AD Joined |
| NO | NO | YES | Domain Joined |
| YES | NO | YES | Hybrid AD Joined |
| NO | YES | YES | On-premises DRS Joined |
Setting up the Group Policy Object
- Open up Group Policy Management Console and create a new group policy object
- Navigate to Computer Configuration > Policies > Administrative Templates > Windows Components > MDM
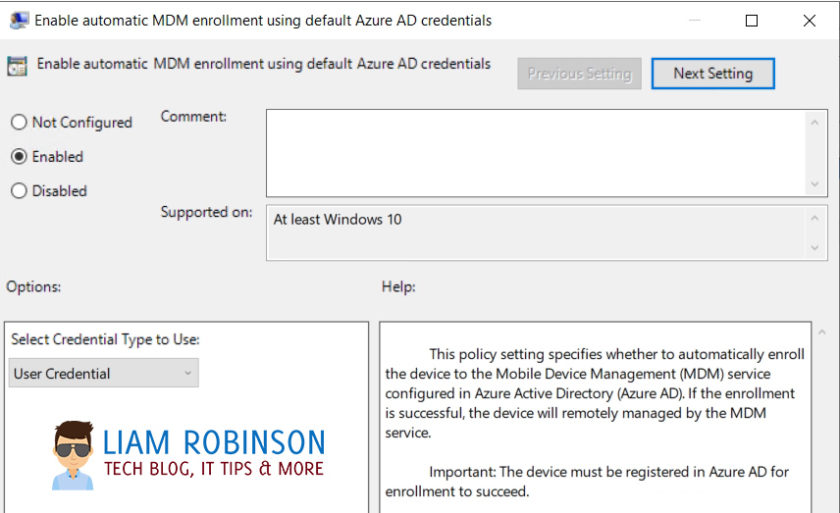
- Double click the setting enable automatic MDM enrollment using default Azure credentials
4. Enable the policy and choose User Credential
5. Deploy the GPO over a test OU
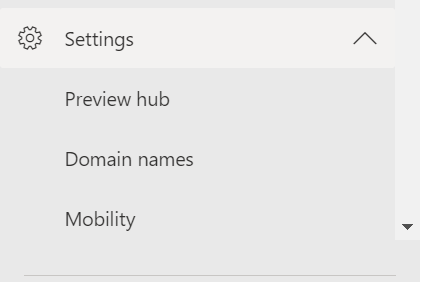
When a user with a valid Intune licence signs into the PC it should now automatically enroll into Intune. The user must also be allowed to enroll devices into Intune to check this head to Azure Active Directory and click Settings > Mobility
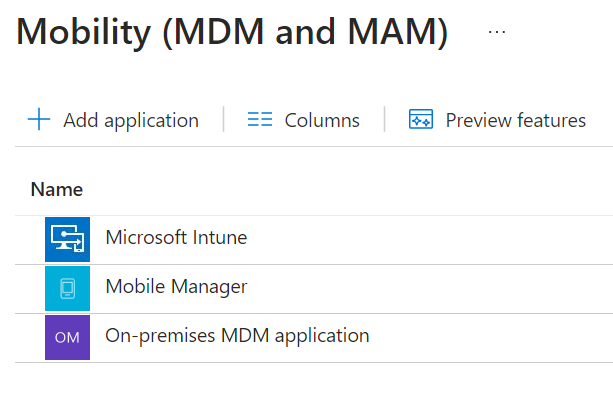
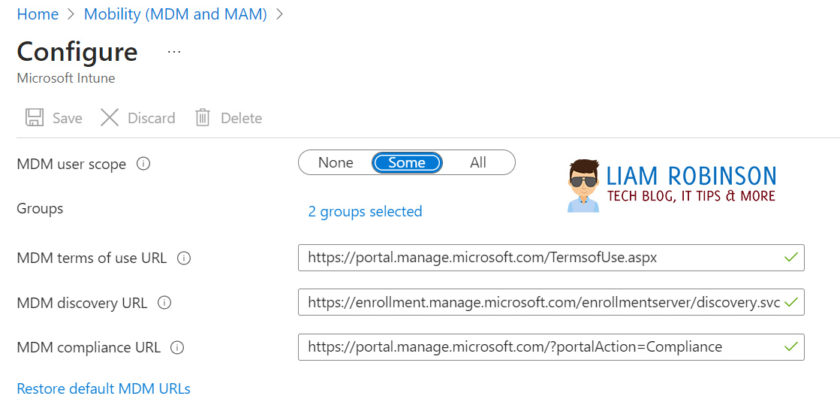
Choose Microsoft Intune
On the MDM user scope, select the users you wish to be able to join devices to Intune, remember they must have a valid Intune licence assigned to them.
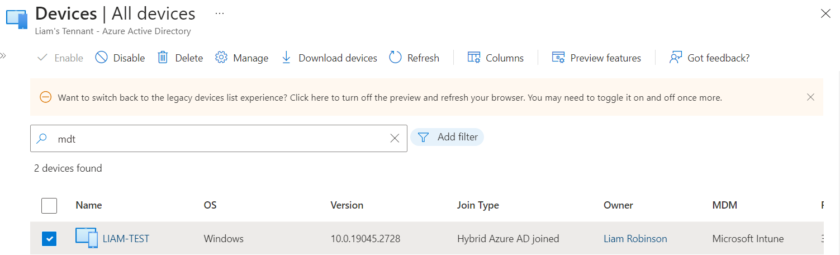
You should now be able to see your device is Hybrid Azure Joined but also joined to the MDM (Intune), head to devices, search for your device and verify its now showing as Hybrid Azure AD Joined and MDM is set to Intune
Known Issue’s
If you are having any issues you can check the logs by going to event viewer on the PC you are trying to join, go to Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider
If you see an error with Auto MDM Enroll: Failed (Unknown Win32 Error code: 0x8018002a) this is down to having MFA enabled. To remedy this you either need to disable MFA (not recommended) or go to Conditional Access and allow an exception in your CA policy (this requires Azure P1 subscription which is included in A3/E3 A5/A5)
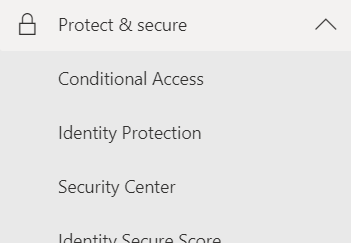
Head to Azure AD admin centre and go to Protect & Secure > Conditional Access
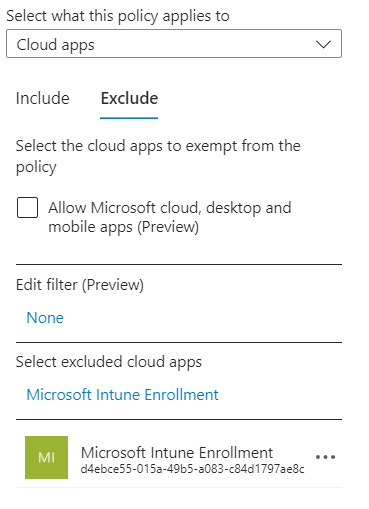
Open your policy and under cloud apps or actions and head to Exclude and search for Microsoft Intune enrollment.
The next time you login the PC should now automatically join intune.

#EdTech Network Manager, experienced in Microsoft 365, Server 2019, Intune, SCCM and anything inbetween.