Deploying Windows 11 efficiently across multiple devices is essential for IT administrators aiming to save time and ensure consistency. Historically, many schools and organisations have relied on traditional methods such as SCCM (System Centre Configuration Manager) or MDT (Microsoft Deployment Toolkit) to create tailored ‘golden’ images for deployment. These approaches involved manually building and maintaining custom images, a time-intensive process prone to errors and delays.
With MDT not officially supporting Windows 11 and is set to be retired by 2027, now is the perfect time to transition to modern deployment solutions. Intune Autopilot offers a more streamlined, flexible, and future-proof way to provision devices. It eliminates the need for imaging, allowing for real-time configuration and application deployment as devices are powered on and connected to the internet.
What is Autopilot?
Microsoft Autopilot is a cloud-based deployment technology designed to simplify the setup and management of Windows devices. It provides a streamlined out-of-box experience (OOBE) for end users while enabling IT administrators to pre-configure devices with organisational policies, applications, and settings. With zero-touch deployment, integration with Azure Active Directory and Microsoft Intune, and flexible options like Azure AD Join or Hybrid Azure AD Join, Autopilot eliminates the need for manual imaging and reduces deployment time. It also supports customisation, remote management, and lifecycle operations, making it ideal for modern, scalable IT environments.
This comprehensive guide walks you through every step to deploy Windows 11 with Intune Autopilot, including how to retrieve the necessary hardware hash from diagnostics (OOBE) or your reseller. The article will cater for both Entra ID Joined (Cloud Only) and Entra ID Hybrid Joined (Domain Joined) Scenarios.
By the end of this guide, you’ll have all the knowledge needed to set up a seamless deployment process, ensuring devices are ready for use straight out of the box.
Prerequisites
There are a few prerequisites you must have before setting up Autopilot to setup devices and these are listed below;
- Entra ID (Azure Active Directory): A valid Entra ID tenant is required for device registration and management.
- Microsoft Intune: Intune is used for device management, application deployment, and configuration policies. You must have a valid Intune licence (Included in A3)
- Windows 11 Pro, Enterprise, or Education license: Devices must be running Windows 11 Pro or higher
Step 1: Import Devices ready for Autopilot Deployment
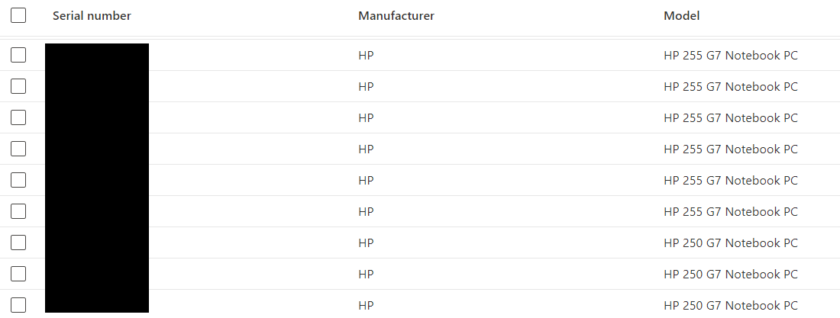
In order to use Autopilot and pre-import our devices, we need their Hardware Hash ID’s and Serial Numbers.
Automatic
The easiest way to obtain this is by asking your Reseller to provide you with this information, this will allow you to import up to 500 devices at a time. The reseller should provide a CSV file containing the Hardware Hash and Serial Numbers. If you are planning on managing lots of devices, i would recommend taking advantage of the ‘GroupTag‘ field to differentiate devices for tailored deployment. For example you could add ‘HPDesktop‘ or ‘HPLaptop‘ to the group tag field. This will assist with assigning Autopilot profiles later on.
Manual
If you can’t obtain the HH and SN’s from your reseller, you can manually export this information from each device by pressing CTRL + SHIFT + D on the OOBE page and exporting the logs to a USB drive. The Log includes a CSV file with the HH and SN. Alternatively you can use the Powershell script from Microsoft to upload the HH directly into Autopilot, eliminating the steps below.
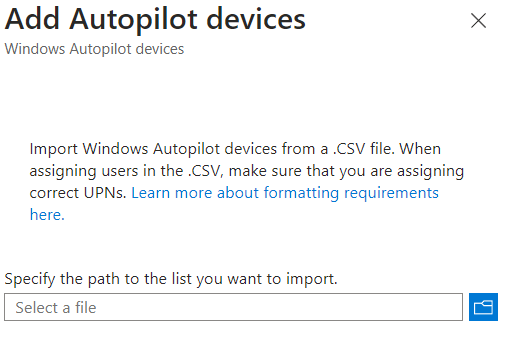
In Intune navigate to Devices > Enrolment >Windows Autopilot > Devices and click Import.
Here you can select the CSV file containing the Hardware Hash and Serial Numbers. Your devices should now show up under Autopilot Devices.
Create Autopilot Device Group
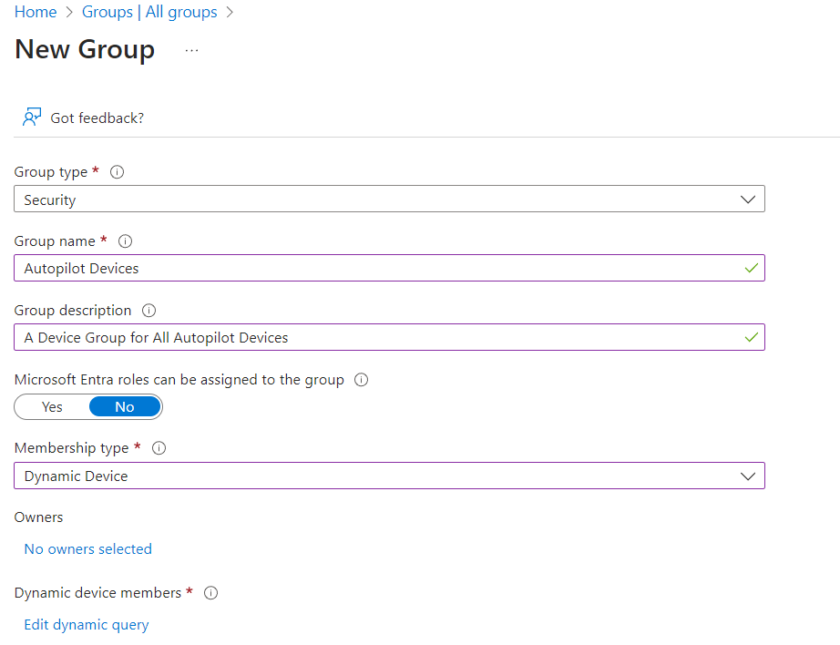
In order to ensure apps, config settings and deployment profiles are applied correctly to Autopilot devices during setup, we want to set up a Dynamic Device Group containing our Autopilot devices. To do this head to Groups > All groups > New Group.
Fill in the required details and select ‘Dynamic Device‘ under ‘Membership Type‘
To ensure devices are added automatically, edit dynamic query and enter the following syntax;
All Autopilot Devices
(device.devicePhysicalIDs -any _ -contains "[ZTDId]")Filtered Autopilot Devices
You can use the GroupTag Field from Step 1 to create different groups for different tags, for example AutoPilotDomain and AutoPilotCloud. This is useful for deploying separate profiles depending on domain join requirements.
(device.devicePhysicalIDs -any _ -contains "[ZTDId]") -and (device.devicePhysicalIDs -any _ -contains "[OrderID]:AutoPilotDomain")(device.devicePhysicalIDs -any _ -contains "[ZTDId]") -and (device.devicePhysicalIDs -any _ -contains "[OrderID]:AutoPilotCloud")Save the Group. You should now begin to see the devices added to your group based on your dynamic device query.
Step 2: Create Autopilot Deployment Profile
To customise your Autopilot deployment you need to create a Deployment Profile or edit the Default Profile. To begin, head to Devices > Enrolment > Windows Autopilot > Deployment Profiles
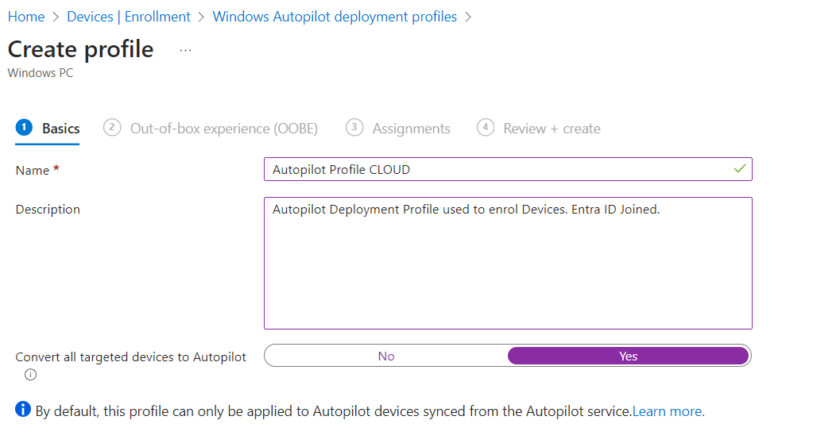
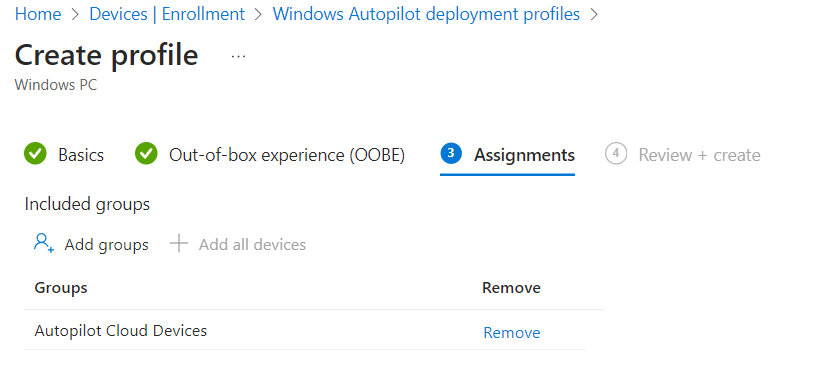
Click +Create Profile and add a new ‘Windows PC‘ profile.
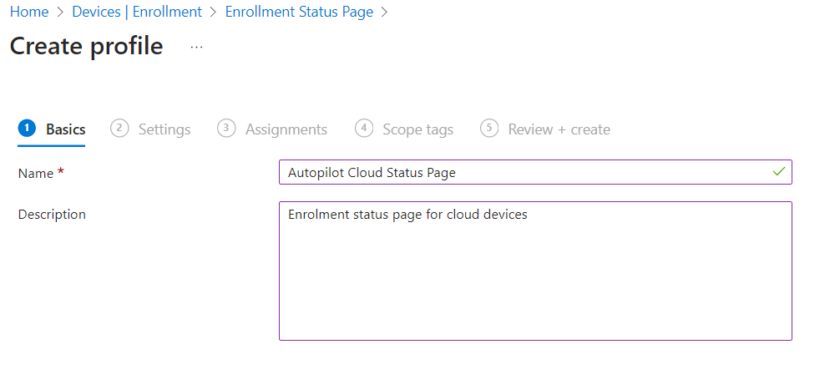
Give your Profile a suitable name and description.
Configure your out-of-box-experience settings. If you plan on enrolling your device(s) as Entra ID Joined (Full Cloud), ‘Self-Deploying‘ deployment mode works perfect for Zero-Touch Installations.
Assign the deployment profile to the dynamic device group you created in step 1 earlier.
If you wish to enrol your devices as Entra ID Hybrid Joined (Domain Joined), you will need to choose ‘User-driven‘ and follow the additional steps below to domain join Autopilot Devices. If not, proceed to Step 3.
2.1: Configure settings for Microsoft Autopilot Domain Join (Optional)
Configure Active Directory / Microsoft Entra Connect Sync (AAD Connect) (Optional)
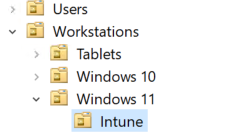
To help keep Active Directory Clean, I recommend creating a new Organisational Unit (OU) in Active Directory called ‘Intune‘ to help you identify which devices are added by Intune/Autopilot.
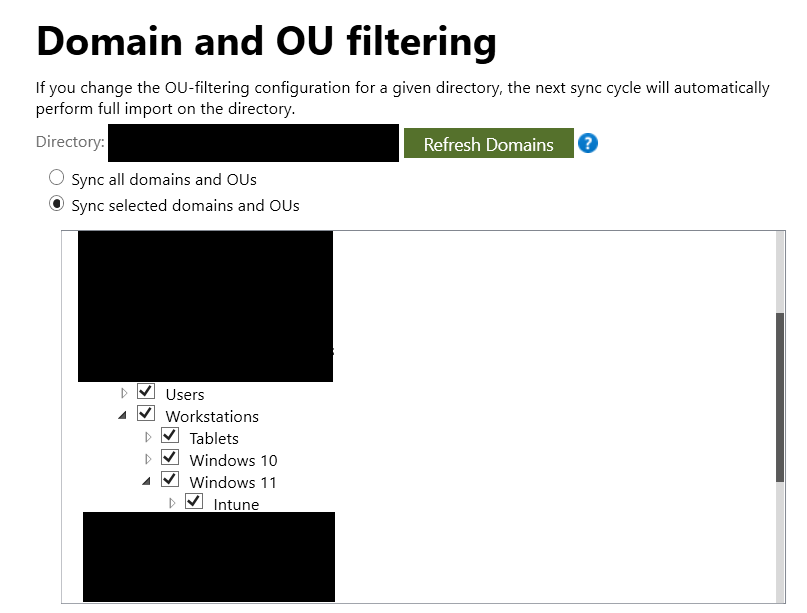
Once you have created this OU ensure it is synced to Entra (Azure Ad) with the Entra ID Connect Tool. You can verify this by opening the Entra ID Connect Tool and clicking Configure.
Under Domain and OU Filtering ensure your OU is set to be synced.
Configure Domain Join Profile (Optional)
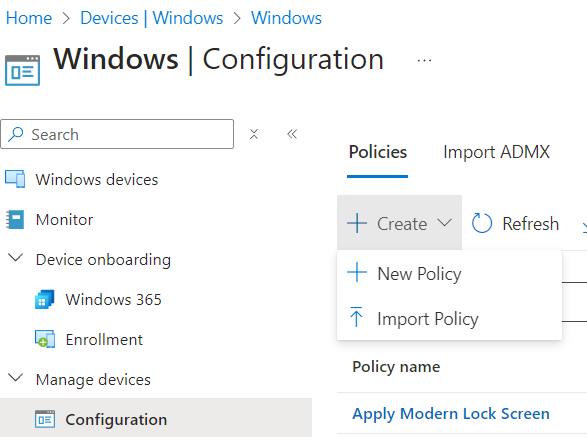
In order to join devices to your domain, you will need to Create a Domain Join policy in Intune. Head over to Devices > Configuration > +Create and add a new policy.
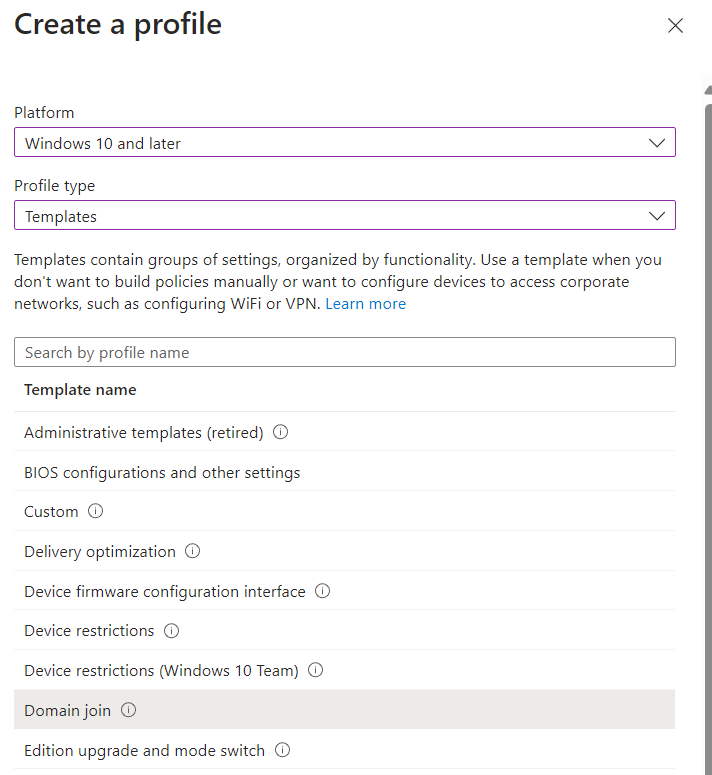
Select Windows 10 and Later > Templates > Domain Join
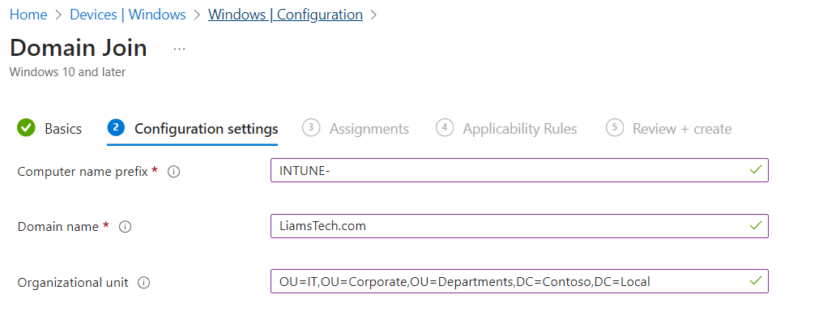
Give your profile a suitable name and configure the domain settings
Apply your Domain Join Profile to the Autopilot Group you created earlier.
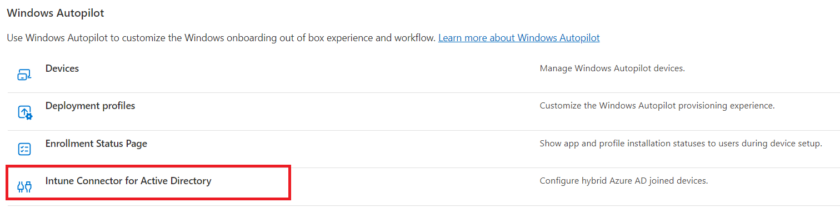
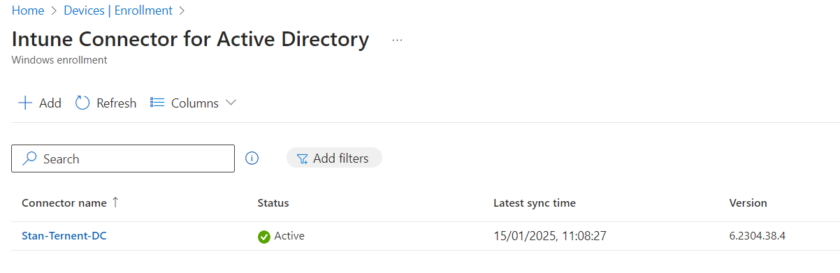
Download and Configure Intune Connector for Active Directory (Optional)
There are many valid arguments for and against going ‘Full Cloud’ or ‘Hybrid’ for Endpoint Management, the main reason for most would be down to legacy systems and printers needing the domain to work. If you are looking to Domain Join your autopilot devices (Entra ID Hybrid Joined) you will first need to download the Intune Connector for Active Directory.
In the Intune Admin Centre Navigate to Devices > Enrolment >Intune Connector for Active Directory.
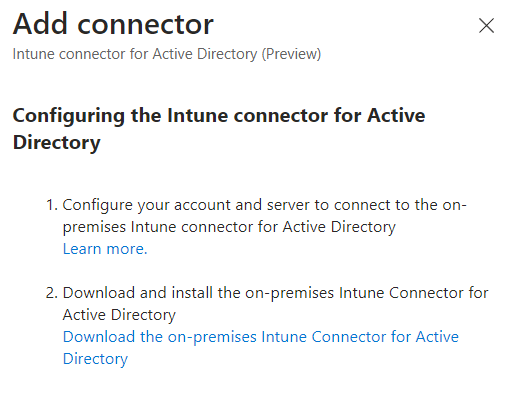
Click Add.
Download the Installer file and Copy it to your AD server.
Run the Installer and configure it by signing in with your admin details.
- The Intune Connector for Active Directory must be installed on a computer that’s running Windows Server 2016 or later with .NET Framework version 4.7.2 or later.
- The server hosting the Intune Connector must have access to the Internet and Active Directory.
- The Account used to setup the Intune Connector must be a global administrator
To verify the Connector has installed, head back to Devices > Enrolment >Intune Connector for Active Directory and verify your server is on the list and showing as Active.
Step 3: Create Deployment Status Page
The enrolment status page appears during initial device setup and during first user sign in. If enabled, users can see the configuration progress of assigned apps and policies targeted to their device. To Start head to Devices > Enrolment > Windows Autopilot > Enrolment Status Page.
Create a New Profile or edit the default profile.
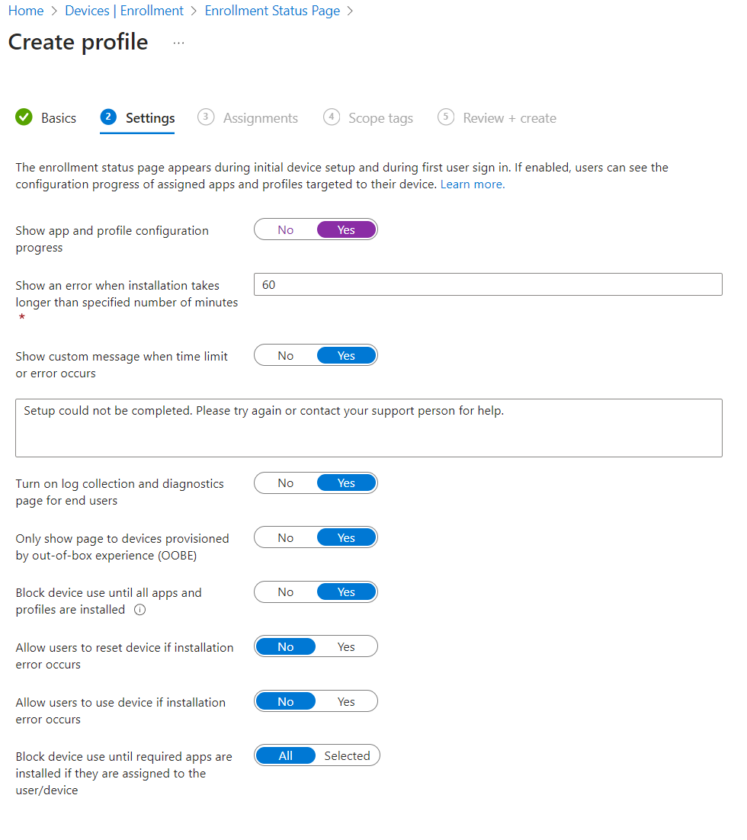
Here you can decide to show the configuration progress to the end user or not. Configure these settings to suit your needs, i find leaving it as default works best.
Assign the profile to your Dynamic Device Group you created in Step 1.
‘Block device use until all apps and profiles are installed‘ – Ensures your devices are fully provisioned with your required apps and settings (Certificates, Safeguarding software etc)
Step 4: Deploy Required Apps
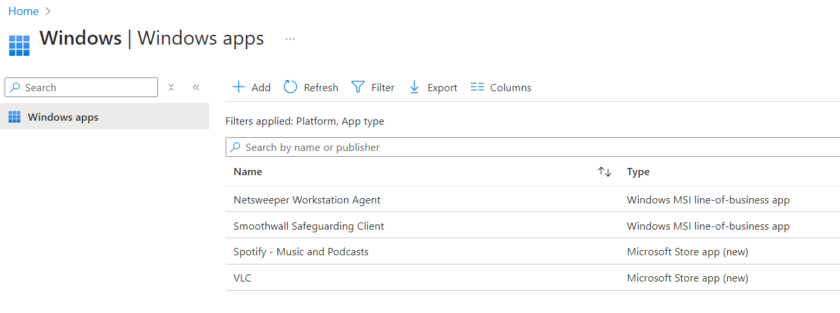
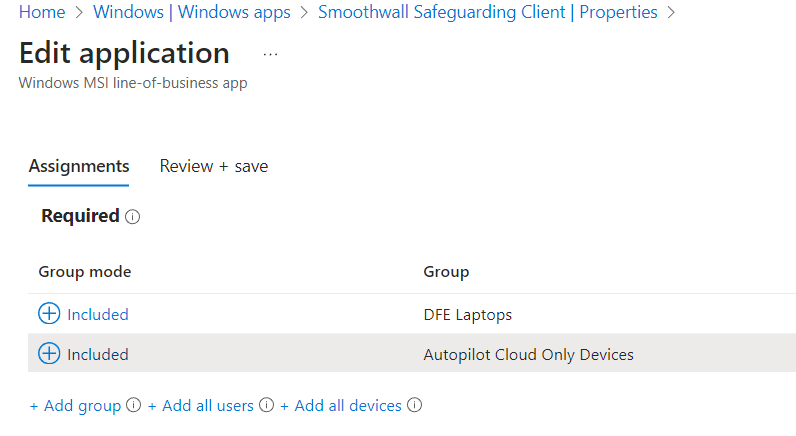
One main reason for imaging machines using traditional methods is the ability to pre-deploy apps before the device reaches the user, in order to replicate this with Intune and autopilot we can simply deploy our required apps from the ‘Apps‘ blade in Intune and selecting ‘Windows Apps‘.
Identify apps you wish to be installed during the provisioning process, for example Smoothwall client click into each app and under ‘Assignments‘ choose the Dynamic Device Group from Step 1.
If you have enabled the ‘Block device use until all apps and profiles are installed‘ setting in Step 3 this will install before the device is provisioned.
Step 5: Trim the fat (Remove Unwanted Apps)
One major downside to deploying PC’s out-of-the-box is the infinite amount of rubbish that comes pre-installed, either from the OEM or Microsoft. If you use MDT or SCCM you can use my free WIMSimple tool to strip unwanted apps from your image file, however this will be no use for deploying via Intune. To combat this I though of developing a little script to clear unused/unwanted apps during provisioning, however after a bit of digging i found there’s already an amazing script out there which does exactly this!
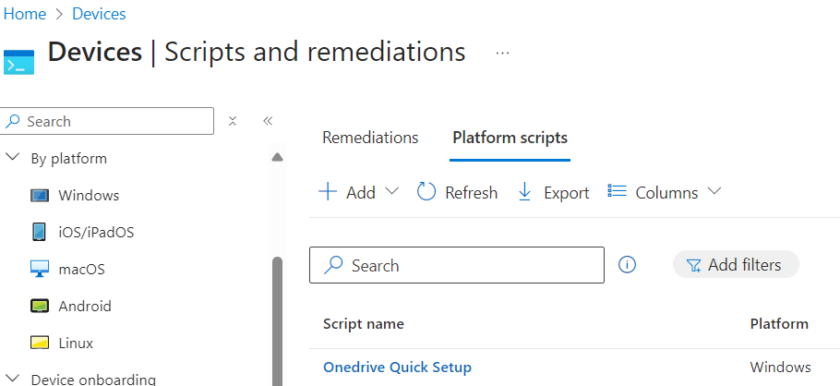
Head over to Andrew Taylor’s Blog and get the latest Intune Debloat Script and save it to your PC.
In Intune head to Devices > Scripts and Remediations. Click Platform Scripts and add new, Windows 10 or later.
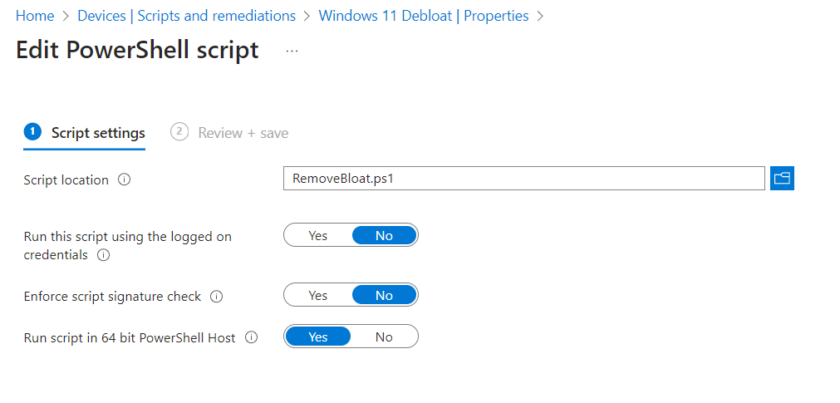
Import the script downloaded from Andrews Blog and change the following settings.
Deploy the script to the same group you created in step 1.
Step 6: Connect your device
Now everything else is configured, simply turn on your autopilot device and connect it to the internet. The device will grab the apps and policies you have setup and provision itself automatically.

#EdTech Network Manager, experienced in Microsoft 365, Server 2019, Intune, SCCM and anything inbetween.



This site is brilliant. Clear, consise, in-depth, and good looking.
I love the layout, and it is a dream to look through. Very clever.
I’d love to put one together for a Mental Health project that I want to start on, what did you use to put it together?
Looks like iot took a while to do, but worth the hard work!
ALl the best.